Connecting to SharePoint that is configured with federated identity authentication (ADFS)
If your SharePoint environment is configured to use a claims-based identity model to control access, as part of the Single Sign On (SSO) realm, our add-in requires that you specify the Active Directory Federated Service (ADFS) information into the login dialog, so that the add-in can negotiate and logon to the STS server (also known as Security Token Service).
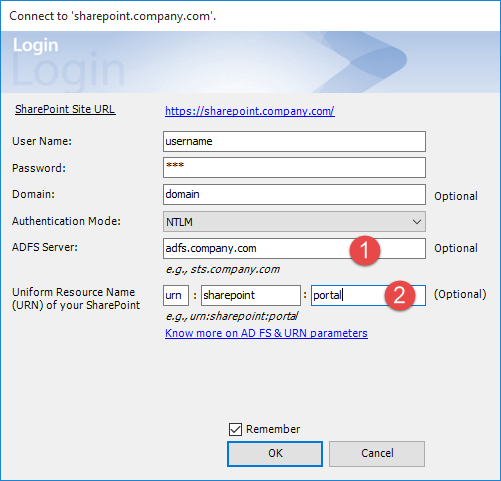
![]() ADFS or STS web address – The value for this URL is the federation service name that will respond to authentication requests from our add-in. It could be in the format of adfs.yourcompany.com or sts.yourcompany.com. Consult your network administrator to know the exact value.
ADFS or STS web address – The value for this URL is the federation service name that will respond to authentication requests from our add-in. It could be in the format of adfs.yourcompany.com or sts.yourcompany.com. Consult your network administrator to know the exact value.
![]() Uniform Resource Name (URN) or simply “realm” that was specified when setting-up a relying party trust in ADFS for your SharePoint site. This realm has a format of urn:a:b where ‘a’ and ‘b’ are two parts you need to specify in the login prompt. For example, if ‘a’ is ‘sharepoint’ and ‘b‘ is ‘portal’, the actual URN will be ‘urn:sharepoint:portal‘
Uniform Resource Name (URN) or simply “realm” that was specified when setting-up a relying party trust in ADFS for your SharePoint site. This realm has a format of urn:a:b where ‘a’ and ‘b’ are two parts you need to specify in the login prompt. For example, if ‘a’ is ‘sharepoint’ and ‘b‘ is ‘portal’, the actual URN will be ‘urn:sharepoint:portal‘
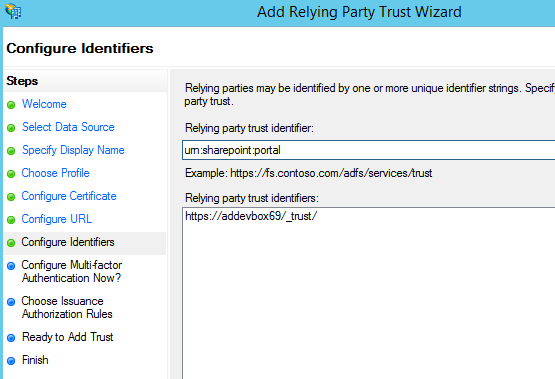
VERY IMPORTANT: In the login dialog prompt, the relying party trust identifier MUST be entered EXACTLY as it is displayed in the AD FS Manager. That means the identifier is CASE SENSITIVE, if the two do not match, the add-in and the trusted identity provider will NOT communicate. If you enter a wrong realm, you might get the following error message:
“ID3082: The request scope is not valid or is unsupported.”
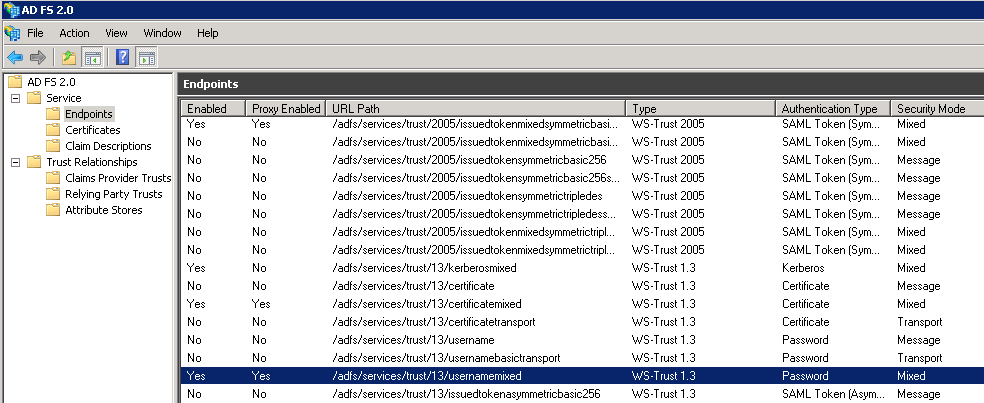
NOTE: In the login prompt, you cannot specify a local user for ADFS authentication. A domain account should be specified for this. Also make sure, the trust/13/usernamemixed endpoint is enabled at ADFS, which should be the case in a default setup: